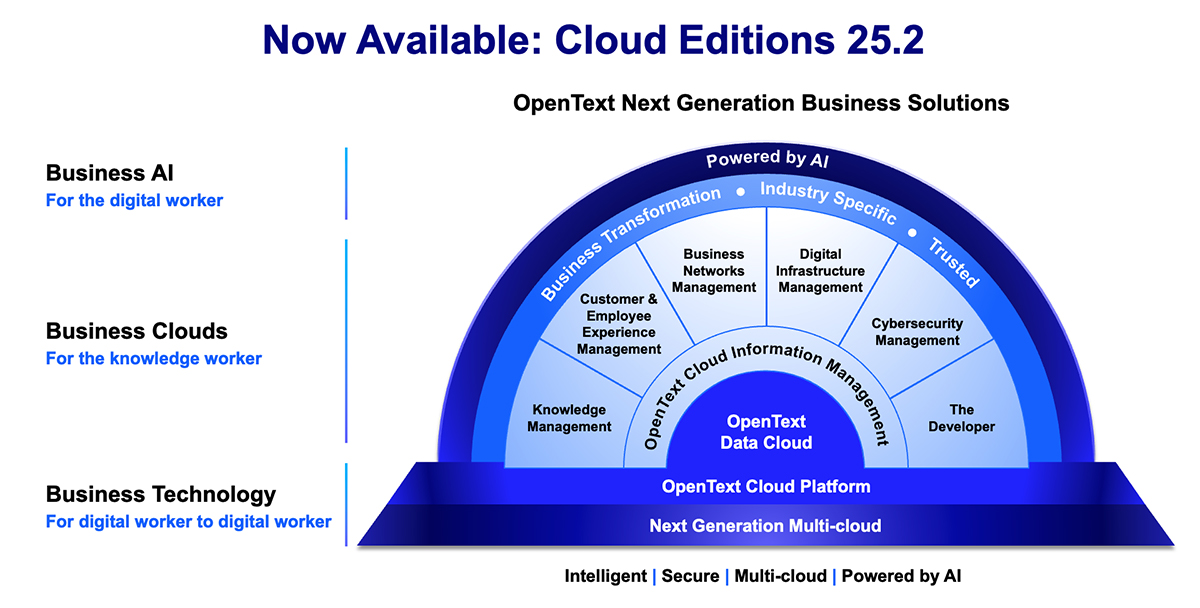
OpenText™ Titanium X (CE 25.2) isn’t just a destination, it’s an experience. We have reimagined how knowledge workers across your organization can elevate their productivity by reimagining what they can do with their information.
Information reimagined
Looking to drive innovation, enhance security, and streamline operations? It’s time to upgrade to Titanium X, the ultimate enterprise solution crafted for tech-savvy leaders and IT professionals ready to take their business to the next level.
- Smarter decisions with AI: Titanium X leverages OpenText™ Aviator and advanced GenAI tools, giving your team the power to automate repetitive tasks with ease (think 120+ AI agents) and focus on what truly matters—strategic, high-impact decisions. With AI-driven insights and optimized workflows, your enterprise gains productivity and efficiency like never before.
- Cloud performance, elevated: Why choose between private or multicloud? Titanium X supports seamless SaaS and hybrid-cloud operations, enabling instant, secure integrations across platforms. Its ready-to-use connectors fuel innovation, helping your business achieve more, faster.
- Next-level security: Don’t just manage threats, outsmart them. Titanium X offers real-time threat detection and unparalleled data protection, keeping your enterprise both compliant and secure. Built for global regulations, it ensures the highest level of trust without compromising flexibility.
Knowledge reimagined
Is your business stuck on legacy systems? It’s time for an upgrade. Titanium X of OpenText™ Content Cloud is here to revolutionize your operations with enhanced capabilities, seamless integrations, and cutting-edge security.
- NextGen efficiency: Legacy systems can’t keep up with today’s demands. With Titanium X of OpenText Content Management, you’ll experience 80 percent faster workflows and 10 times faster content retrieval, thanks to AI-powered document workflows and automation. Time to say goodbye to manual processes.
- Cloud freedom, simplified: Tired of data silos and IT headaches? Titanium X offers multi-cloud flexibility and centralized control, providing 10 times greater reliability in the cloud, while cutting costs and speeding deployment. Adopt the cloud model that suits your business without the chaos.
- Seamlessly connected apps: No more toggling between apps! Titanium X syncs effortlessly with tools like Microsoft 365, Salesforce, and SAP, driving 350 percent higher employee productivity.
- Enhanced user experiences: Outdated, clunky interfaces? Not with Titanium X. Expect personalized, intuitive designs tailored for team roles and realize savings up to $5M.
- All-around modern security: Don’t play with fire—upgrade to next-gen security like zero- trust architecture and adaptive protocols. Stay secure, everywhere.
Conversations reimagined
Are legacy systems holding your customer success and marketing teams back? If you’re stuck with manual processes, clunky integrations, or outdated compliance workflows, it’s time to level up with Titanium X of OpenText™ Experience Cloud for your customer communications.
- Reduce manual tasks: With Titanium X you can improve content workflows by 83 percent, cut asset search time by 96 percent, and get your content to market faster. Spend less time on repetitive tasks and more time achieving results.
- Cloud-native scalability: Titanium X drives 40 percent faster revenue growth with unbeatable scalability, cloud provisioning, and lower infrastructure costs. Modernize customer success with scalable and affordable communications and messaging.
- Seamless integrations: Say goodbye to compatibility headaches. Pre-built integrations (Salesforce®, SAP®, Microsoft SharePoint®, and more) with CPaaS deliver greater efficiency than ever before.
- Ironclad compliance: Stay protected with automated compliance for HIPAA, PCI DSS, and more. OpenText™ Experience Cloud reduces compliance and accelerates audit reporting by 90 percent.
Security reimagined
Cyber threats are evolving, and traditional security measures just can’t keep up. Titanium X of OpenText™ Cybersecurity Cloud isn’t just an upgrade—it’s a game changer for security operations teams. Here’s why:
- Faster threat detection and response: Manual threat detection is slow and resource-heavy. Titanium X leverages autonomous AI-driven tools for 5 times faster threat detection. With faster insights you can tackle attacks before they escalate.
- Simplified security management: Managing multiple tools across hybrid and cloud environments is inefficient and risky. Titanium X offers seamless integration with a unified interface, reducing security management complexity by 50 percent. It also accelerates incident response by up to 70 percent, because every second counts.
- Streamlined compliance and reporting: Regulatory compliance doesn’t have to be a headache. Titanium X features built-in tools for GDPR, HIPAA, and PCI DSS, streamlining compliance and reporting and driving 65 percent faster audit readiness.
- Greater efficiency: Boost SOC efficiency by up to 30 percent with Titanium X’s hyper-personalized UI that simplifies operations and eliminates the hassle of complex interfaces.
Connections reimagined
Struggling to keep your supply chain running smoothly? Say goodbye to inefficiencies and hello to Titanium X of OpenText™ Business Network Cloud, a game changer for supply chain managers and operations executives. Here’s why Titanium X is a must-have:
- Real-time collaboration: Outdated trading platforms cost time and money. OpenText™ Business Network Cloud enables instant collaboration between suppliers, manufacturers, and logistics providers, streamlining operations for a 317 percent ROI in three short years. Faster disruptions response? Check. Happier customers? Double-check.
- Automated processes: Banish manual data entry forever. OpenText™ Trading Grid integrates seamlessly with leading ERP systems like SAP, Oracle NetSuite, and Microsoft Dynamics™, automating procurement and order processing. Gain 30 percent more productive supply chain teams—because your team’s time is priceless.
- Predictive AI insights: Siloed data? Not anymore. With AI-powered analytics, OpenText™ Trading Grid Command Center accurately forecasts demand and mitigates supplier risks. The result? An 18 percent faster order/product delivery time across the board.
- Compliance made easy: Avoid costly fines for missed regulations. Titanium X simplifies global e-Invoicing and regulatory mandates, with 24/7 e-invoice processing.
CloudOps reimagined
It’s time to bid farewell to inefficiencies and hello to smarter Observability and Service Management with Titanium X. Wondering what’s in it for you? Here are the game-changing benefits that make upgrading a no-brainer:
- Centralized observability: Stop playing hide and seek with issues in your multicloud environments. Titanium X offers 49 percent fewer outages and proactive blind spot elimination.
- AI-powered automation: Why waste hours on repetitive tasks? With a 31 percent decrease of issue resolution time, Titanium X lets you focus on what truly matters—no more error-prone busywork.
- Faster problem resolution: Say goodbye to delays and guesswork! Go from hours to seconds for Mean Time to Resolution (MTTR) with AI-powered tools that simplify troubleshooting.
- Streamlined workflow: Too many tools and too little time? Titanium X cuts the chaos with 30 percent fewer IT tools and streamlined processes, saving you time and headaches.
- Stronger security: Titanium X strengthens your defenses with automated patching and compliance tools. Go from weeks to hours for fixes and greater peace of mind.
Engineering reimagined
Still wrestling with manual processes for DevOps, endless context-switching, or last-minute software production headaches? It’s time to upgrade your software delivery toolchain with Titanium X—a game-changer for developers striving for speed, efficiency, and excellence in their workflows.
- Automate everything: Manual reviews slowing you down? Titanium X of OpenText™ DevOps Cloud automates code quality checks, release approvals, and test coverage with AI-powered insights, so you focus on the work that matters. Enjoy 50 percent faster AI-powered deployments and 75 percent faster test execution.
- Effortless integration: Tired of constant tool-switching? Titanium X offers pre-built integrations and open APIs that seamlessly connect your ecosystem. Skip the hassle of workarounds with 50 percent fewer CI/CD failures.
- Security without bottlenecks: No more scrambling through last-minute audits. OpenText Software Delivery Platform (now available in SaaS) delivers automated security and compliance checks with 95 percent of tests automated.
- Debug smarter, not harder: Finding bugs shouldn’t feel like detective work. Upgrade for AI-driven debugging and find the root cause in seconds, not hours.
Decisions reimagined
Facing sluggish data processing, spiraling costs, or inefficient workflows? It might be time to ditch the old system and upgrade to Titanium X of OpenText™ Analytics Cloud—the AI-powered solution that promises speed, scalability, and security like never before.
- Unparalleled performance: Titanium X of OpenText Analytics Cloud doesn’t just perform—it accelerates. Experience up to 50 percent faster queries with AI-optimized indexing and 40 percent downtime reduction. Say goodbye to delayed insights and hello to data-driven decisions at lightning speed.
- Cost efficiency meets scalability: Cut costs smarter, not harder. With Titanium X of OpenText Analytics Cloud, enjoy 70 percent archive retrieval reduction. Bring customer apps to market 35 percent faster.
- Game-changing automation: Streamline your workflows with AI-driven automation. Titanium X of OpenText Analytics Cloud reduces manual data preparation, while no-code ML deployment saves time and effort with models that learn and adapt faster.
- Rock-solid security: Protect what matters most. With enterprise-grade encryption, zero-trust architecture, and real-time threat detection, your data stays secure. Reduce breaches and save on the average $4.45M those incidents cost companies.
Are you ready?
Experience the Titanium X difference today. Whether you’re looking to automate processes, strengthen security, or employ smart AI, upgrade to Titanium X to accelerate your journey.
Learn more about Titanium X (CE 25.2)Additional resources:
- Check out Titanium X guided tours and demos
- Don’t get left behind. We make modernizing easy. Contact us to help plan your upgrade
- Need help upgrading? OpenText Professional Services can help
- Want to see more? Schedule a demo