Quantum computing may not be mainstream yet, but the clock is ticking — and attackers know it. The “Harvest Now, Decrypt Later” (HNDL) threat means adversaries are stealing encrypted data today, banking on quantum computers to crack it tomorrow. Meanwhile, AI – especially Agentic AI – is evolving faster than most organizations can govern it.
To explore how enterprises can defend against both fronts, I sat down with three of my OpenText Enterprise Cybersecurity peers:
- Tim Sedlack – Product Management Lead, Data Security
- Tim Bramble – Product Management Lead, Threat Detection & Response
- Phil Sewell – Veteran Subject Matter Expert in Data Protection & Secure Analytics
Q & A Panel on Quantum Computing and Agentic AI
Tim Sedlack (Data Security)
Greg: Everyone’s talking about quantum breaking encryption. What’s the advantage of symmetric encryption and tokenization in that fight?
Tim S: That’s a great question! Think of it like being dealt two aces — symmetric encryption and tokenization. Together, they give you a winning hand against quantum threats.
Symmetric encryption doesn’t rely on prime number factorization, unlike asymmetric encryption, and that’s the danger. Quantum computers can do the math, and fast! Symmetric encryption avoids this weakness entirely, since there’s no public key to download and attack. NIST and the US DoD recognize symmetric encryption as the only acceptable quantum-resistant encryption technique in the Commercial National Security Suite. If you’re using symmetric encryption of at least 256-bit strength, you’re safe today and in the immediate future.
Tokenization is the second ace. It replaces sensitive data with tokens from a randomly generated lookup table. Without that table, the original data cannot be reconstructed –no matter how much computing power is available, even with quantum. That makes it computationally infeasible to reverse-engineer the data, protecting it far beyond the reach of brute force.
*Guardrail in Action: Deploy 256-bit symmetric encryption and tokenization today to render stolen data useless against both current and future threats.
Greg: And what about harvest now, decrypt later attacks? Can persistent encryption and tokenization protect against that?
Tim S: Yes – persistent encryption and tokenization are built for long-term defense. The HNDL threat is real: attackers are exfiltrating data now, betting they can decrypt it later with quantum computers. This is why enterprises must ensure their protections are quantum-safe today.
Format-preserving encryption and tokenization solutions are now available. This ensures that even if bad actors steal data, it will remain protected well into the quantum era.
*Guardrail in action*: Don’t wait for quantum – protect data now with persistent encryption and tokenization that will hold up tomorrow.
Tim Bramble (Threat Detection & Response)
Greg: While quantum is a future threat, AI-driven attacks are here now. How do you keep pace with adversaries using Agentic AI?
Tim B: AI-driven attacks are already reshaping the threat landscape. Agentic AI lets adversaries move faster, scale operations, and launch sophisticated campaigns with far less expertise than ever before. The volume and speed of these attacks far outpace manual defenses.
That’s why a human + machine partnership is critical. Defenders must lean on AI to detect and respond to evolving behaviors, just as adversaries use it to attack. In this environment, behavior constantly shifts – meaning detection and remediation tools must be AI-driven by design.
*Guardrail in Action: Develop a human-AI defence model that matches the scale, speed, and adaptability of Agentic AI-driven threats.
Greg : How do AI governance and identity governance fit into that?
Tim B: AI governance and identity governance are two sides of the same coin. Identity governance defines the who, while AI governance defines the how. Identity governance
ensures that only the right people, processes, or AI agents can access sensitive systems, while AI governance sets the boundaries for what those agents are allowed to do.
This combination is critical because AI agents are not only valuable tools for defenders but also potential targets – and even weapons – for attackers. They expand the attack surface in ways that organizations must carefully manage.
Many advanced threats today hinge on identity-related attacks, such as insiders misusing valid credentials. Defending against these requires strong identity controls and the ability to detect and respond to attempts at misuse. That’s the role of Identity Threat Detection and Response (ITDR). When paired with effective AI governance, ITDR helps ensure both human and machine identities remain trustworthy — and that their use by AI systems, whether internal or adversarial, stays within intended boundaries.
*Guardrail in Action: Pair AI governance + ITDR to protect both human and machine identities in an AI-driven world.
Phil Sewell (Data Protection & Analytics)
Greg: You’ve helped customers protect and analyze sensitive data for over 15 years. How is this AI + quantum era changing the conversation?
Phil: The stakes have never been higher. Quantum computing is forcing executives to rethink encryption, while AI is driving massive demand for data. Together, they’ve pushed cybersecurity from a back-office concern to a board-level priority.
Organizations must take stock of today’s cryptography and build quantum-resistant data security strategies. At the same time, AI requires huge datasets for training – but those often contain sensitive or personally identifiable information (PII). Making such data widely available without strong safeguards magnifies risk.
*Guardrail in Action: Invest in quantum-safe encryption + privacy-preserving data controls to fuel AI innovation without exposing sensitive information.
Greg: And differentiation – where does OpenText stand apart?
Phil: We enable safe data use without sacrificing business value. For over a decade, we’ve helped organizations protect data for analytics by using advanced de-identification
techniques. These methods let sensitive data be ingested into AI/LLM models while preserving – or even enhancing — its business utility.
Our platform stands out for its flexibility: customers can apply the right protection pattern based on the sensitivity and risk profile of their data. Combined with quantum-safe readiness, identity protection, and AI governance, OpenText provides a holistic framework for securing the data-driven enterprise.
*Guardrail in Action: Choose flexible data protection patterns that let you power AI while preserving trust and compliance.
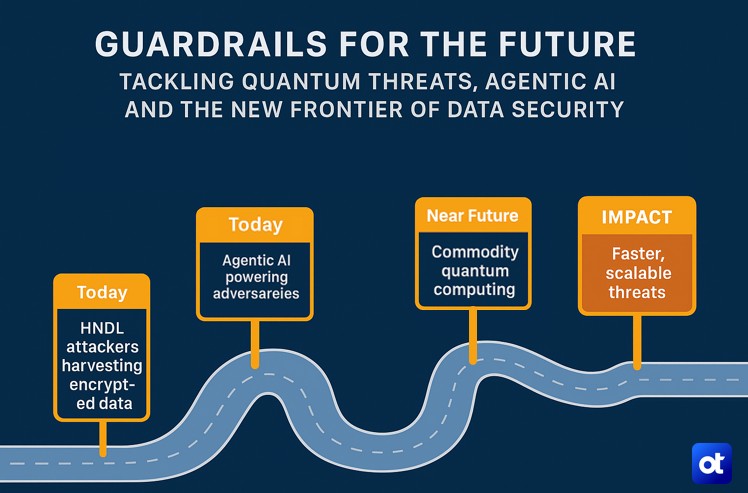
Final thoughts
From the quantum-safe resilience of symmetric encryption and tokenization to the governance guardrails that keep AI in check, OpenText is building a security framework designed for both today’s threats and tomorrows.
Because the real challenge isn’t choosing between defending against Agentic AI now or quantum later – it’s winning on both fronts.
Interested in learning more about countering today’s AI-enabled threats while preparing for the disruptive impact of quantum computing? OpenText recently partnered CIO magazine to poll a range of data security experts on the challenges and opportunities presented by quantum computing. Read The dual threat of AI and quantum computing: IT leaders brace for the next data security era to read their responses and advice.
Explore how OpenText helps you protect sensitive data across AI and quantum use cases.

