Effective threat detection demands speed, precision, and accurate contextualization. Unfortunately, traditional manual methods for mapping security events to frameworks like MITRE ATT&CK can be tedious, error-prone, and insufficient for today’s rapid cybersecurity operations. Fortunately, Retrieval-Augmented Generation (RAG) and Agentic AI have emerged as game-changing solutions, dramatically enhancing how security teams identify, understand, and respond to threats.
RAG and Agentic AI bring automation, context-aware intelligence, and proactive investigation capabilities to cybersecurity, significantly boosting accuracy, efficiency, and responsiveness. Let’s delve deeper into these powerful techniques.
Understanding retrieval-augmented generation (RAG)
Large Language Models (LLMs), while highly advanced, frequently encounter challenges when tasked with providing detailed, precise, or up-to-date information from authoritative sources. This limitation is exactly where Retrieval-Augmented Generation (RAG) steps in, significantly enhancing the capability of LLMs.
RAG operates by dynamically retrieving relevant information from authoritative knowledge bases, such as the MITRE ATT&CK framework, documentation, websites, reports, logs, or any structured or unstructured data repositories. This ensures that responses are contextually accurate and based on current, validated data.
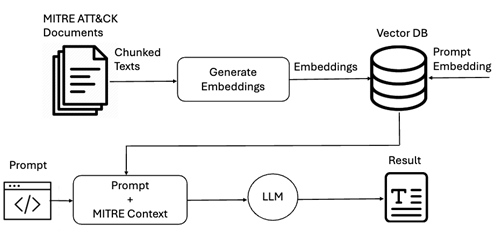
Technical breakdown of RAG implementation
Step 1: Knowledge base preparation
- Collect authoritative cybersecurity documents and resources.
- Break down these resources into manageable, smaller text segments or chunks.
- Generate embeddings (digital representations) for each text chunk using sentence transformers.
- Store these embeddings efficiently within a vector database.
Step 2: Contextual information retrieval
- Accept a cybersecurity-related query or prompt.
- Convert the input prompt into embeddings.
- Query the vector database, using similarity metrics, to identify and retrieve the most relevant context segments.
Step 3: Generation of contextually accurate reports
- Combine retrieved context with the original prompt or event details.
- Use an LLM to synthesize and generate a comprehensive, contextually relevant report.
- The final output clearly links detected events or anomalies to specific adversary tactics, techniques, and procedures (TTPs), supported by authoritative evidence.
Visualizing the process: Consider an example where the security monitoring system identifies unusual activity within endpoint logs. The RAG process triggers immediately:
- Relevant MITRE ATT&CK documentation segments are retrieved from the vector database.
- These segments combine seamlessly with incident-specific details.
- A clear and detailed summary is generated, pinpointing exact adversarial behaviors and suggesting actionable mitigation strategies.
With RAG, security analysts can swiftly and accurately associate suspicious events with known threat activities, vastly improving both the response time and quality of security operations. But RAG isn’t the only game changing technology we are applying to security operations.
Join us at RSAC 2025!
April 28-May 1 at the Moscone Center, San Francisco. Visit us at Booth N-4535 to see live demos or speak to our experts.
Get the details!Agentic AI: Your autonomous cyber investigator
While RAG excels in enriching responses, Agentic AI extends these capabilities by autonomously interacting with external data sources to proactively investigate security alerts and suspicious indicators.
What sets Agentic AI apart? Agentic AI refers to intelligent AI-driven agents powered by LLMs and automated workflows. Unlike conventional, passive AI systems that wait for instructions, Agentic AI actively engages external databases, APIs, and threat intelligence services independently, gathering relevant data and generating insights proactively.
A practical scenario: Agentic AI in action
Imagine your organization’s security system identifies suspicious network activity or an unusual file execution. Traditionally, analysts would manually query threat intelligence databases, an approach that is both time-consuming and prone to human oversight.
With Agentic AI, the moment suspicious indicators (like IP addresses or file hashes) are flagged, the AI agent autonomously initiates queries against threat intelligence databases (e.g., BrightCloud). The agent instantly retrieves critical insights, such as malware classification, historical threat data, and community feedback.
After retrieval, the Agentic AI evaluates the data’s severity and relevance, automatically generating concise, actionable reports. These reports clearly indicate identified threats, potential impact, and practical recommendations for mitigation, significantly enhancing response speed and operational accuracy.
Why implement Agentic AI in cybersecurity?
- Accelerated response: Dramatically shortens threat analysis cycles through automation.
- Enhanced precision: Removes human error by systematically retrieving comprehensive threat intelligence.
- Analyst empowerment: Relieves analysts from repetitive tasks, allowing greater focus on complex and strategic analyses.
- Continuous threat intel updates: Integrates real-time updates from external threat sources into internal security processes.
Future potential of Agentic AI
The evolution of Agentic AI promises even greater enhancements, including proactive threat hunting, real-time multi-source intelligence integration, and automated threat remediation. The future cybersecurity landscape might feature seamless AI agent collaboration across multiple platforms, creating comprehensive, automated, end-to-end security workflows.
Conclusion: The power of combining RAG and Agentic AI
By combining Retrieval-Augmented Generation (RAG) and Agentic AI, cybersecurity teams achieve unmatched capabilities for swiftly identifying, deeply contextualizing, and effectively responding to threats. RAG ensures accurate, authoritative context for incident reporting, while Agentic AI autonomously enriches investigations through proactive intelligence retrieval.
Together, these advanced AI methodologies transform cybersecurity operations, significantly enhancing an organization’s security posture, operational efficiency, and threat resilience. With RAG and Agentic AI in your cybersecurity toolkit, you’re not just reacting to threats—you’re proactively staying ahead of adversaries.
Join OpenText Cybersecurity data scientists @ RSA 2025 where my colleagues and fellow data scientists, Nakkul Khuraana, and Hari Manassery Koduvely, will discuss ‘How to Use LLMs to Augment Threat Alerts with the MITRE Framework.’



