In Network Detection and Response (NDR) related operations, there is often a need to replay a Packet Capture (PCAP) data stream. The reasons can be multiple including verifying operation of supplied detections against known traffic, gathering evidence of an attack where no detections were available, or using PCAP samples to write broader detections. It is not always practical to have full “off the wire” capture infrastructure in place. Utilizing the OpenText™ Network Detection and Response platform and an open-source tool for replaying PCAP, we can demonstrate an approach to replay traffic using OpenText NDR.
More specifically, we will explore how to use a sample of PCAP and replay it against an existing NDR installation using the TCP Replay method. TCP Replay is a tool used to replay network traffic from PCAP files of previously recorded traffic. NDR is typically deployed in an environment where live capture is required, such as on-premises or cloud environments where production workloads take place. NDR Sensors connected to their feed(s) take a copy of the data and write it to disk. NDR also sends session metadata and alerts to the back end for further analysis. The TCP Replay method is especially useful for targeted hunts or secondary analysis which are needed whether you are updating existing detections or creating new ones.
Let’s get started!
Configure sensor to receive traffic
We’ll need to choose a tunnel protocol to replay the PCAP to the sensor. In NDR, there are two tunnel protocol choices in addition to any physical capture cards that may be present: VXLAN and GRE. For the purposes of this exercise, we’ll be using VXLAN. However, the steps to configure a NDR sensor for GRE are similar. Simply use the GRE configuration fields and leave the VXLAN fields blank in the sensor settings.
- Step 1 – Navigate to the NDR Central Management Console (CMC) and login.
- Step 2 – Navigate to Sensors and click on the ‘Gear’ icon for the registered sensor you wish to utilize for the replay.
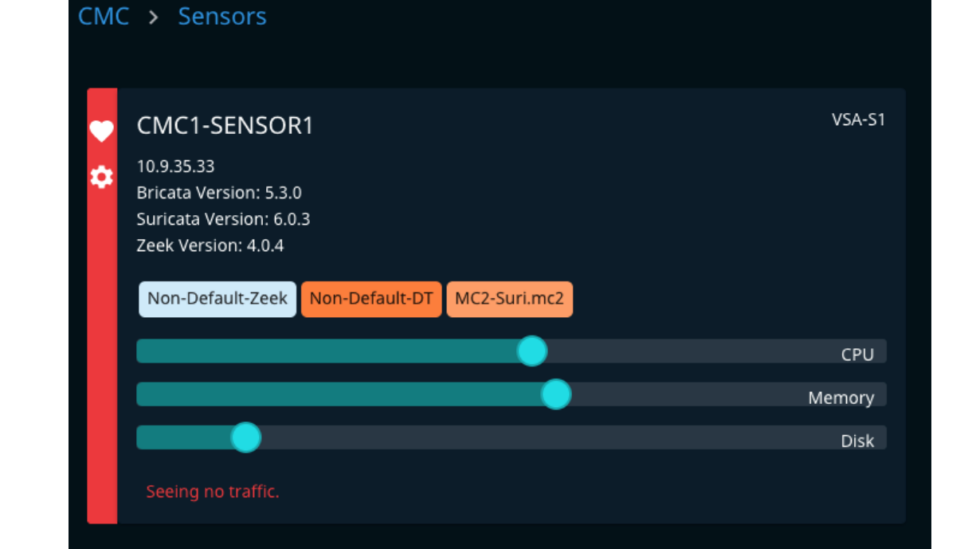
- Step 3 – In the VXLAN configuration area, fill in the VXLAN ID, Destination Port, and MTU. Note this information for use later in the TCP Replay system setup.
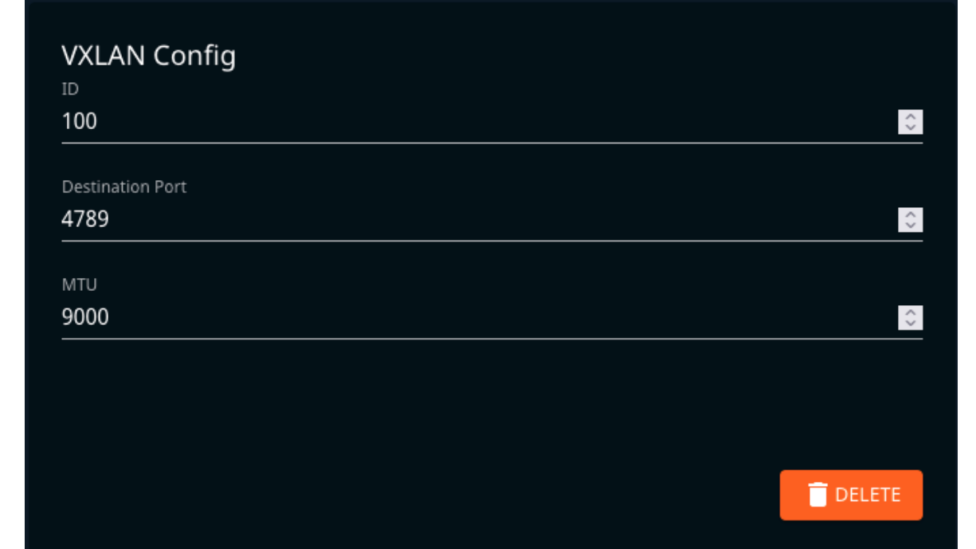
- Step 4 – Save the configured options by clicking the Update button directly under the VXLAN configuration box
TCP Replay System
Next, we need to configure the TCP Replay system to “replay” the PCAP to the sensor. There are 2 main configurations to complete prior to attempting to playback PCAP; the VXLAN tunnel and the TCP Replay session using PCAP you’ve already uploaded to the file system.
Step 1:
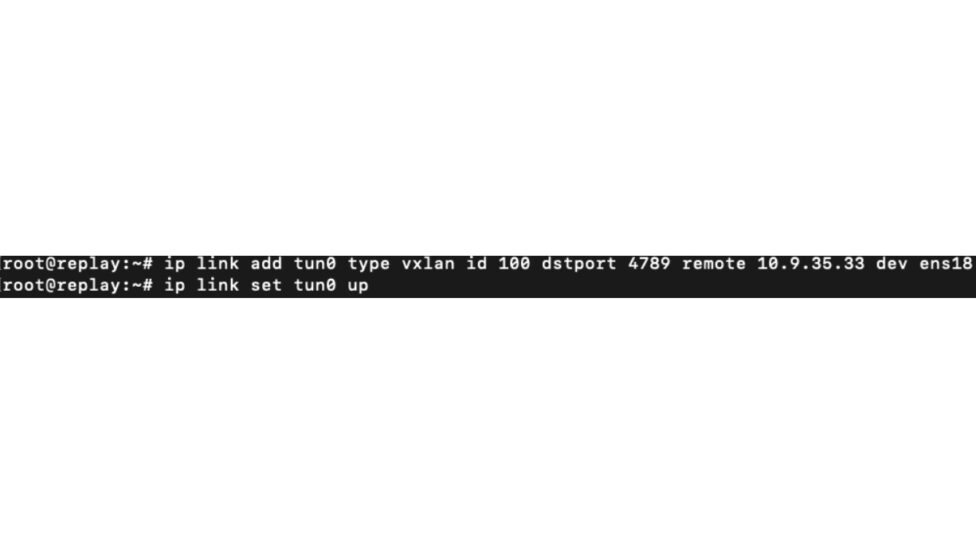
As root or using sudo, set up a VXLAN tunnel to your sensor’s IP interface with the below command sets. (please note: variables have been used in these commands, please replace $vxlan_id, $sensor_ip, and $dstport with information noted in the sensor configuration above. Replace $source_int with the ethernet interface information from your Linux system being used for TCP Replay.
- “ip link add tun0 type vxlan id $vxlan_id dstport 4789 remote $sensor_ip dev $source_int”
- “ip link set tun0 up”
No output is expected from each command unless an error has occurred. You can check the tunnel’s status by running “ip link” command.
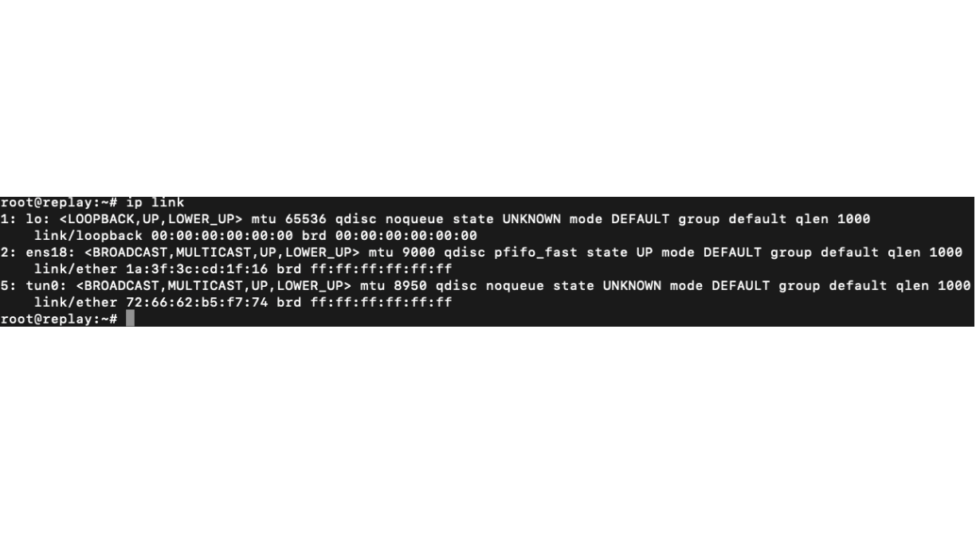
Step 2:
Check to ensure the VXLAN tunnel has been established by using: “ip link” and look for “tun0” with a status of “up”.
Step 3:
In this example, we will play back our PCAP files at 100 Mbit on infinite loop against interface tun0. Alternatively, you may run the replay continuously and perform a CTRL+C when finished.
As root or using sudo:
- “tcpreplay -i tun0 pcap.file” – This will play the file once against the VXLAN tunnel.
- “tcpreplay -i tun0 -l 0 pcap.file” – This will play the file in a continuous loop against the VXLAN tunnel.
- “tcpreplay -i tun0 -l 0 –mbps 100 pcap.file” – This will play the file in a continuous loop at 100 Mbit against the VXLAN tunnel.
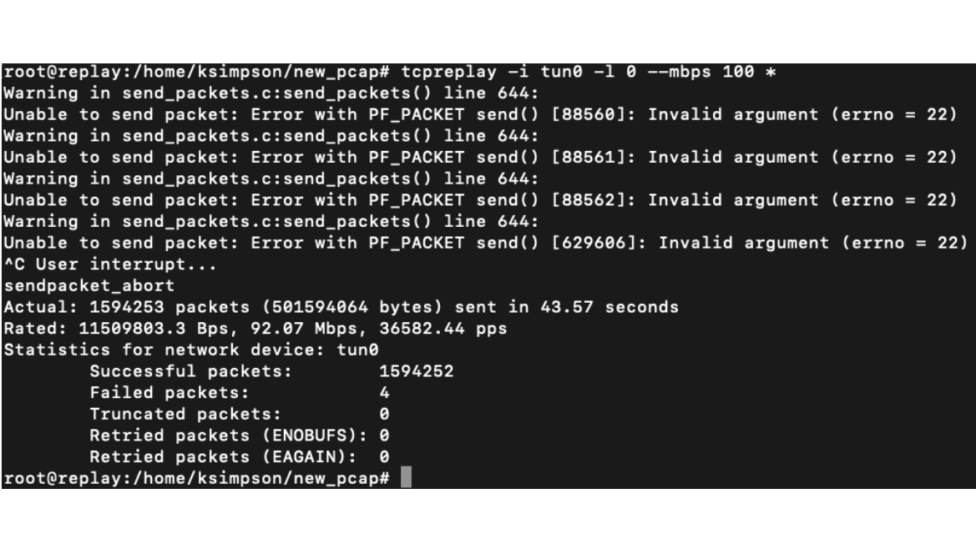
Step 4:
Return to the CMC’s Interface and you should see the expected data in the Alerts and Metadata data streams area. Ensure that you have a baseline data tuning policy and metadata generation enabled. As well, ensure that you have any Suricata signatures you wish to test.
The above has demonstrated how to utilize OpenText NDR to replay and ingest PCAP. This is extremely useful for lab environments, for writing custom detections, and investigating traffic generated from 3rd party platforms. In a future blog, we will explore a backtesting sensor appliance which simplifies this process greatly!
OpenText Cybersecurity Services are available to advise, guide and assist with Network Detection and Response, tuning and optimizing detection capabilities and threat hunting activities. Contact our team today for help with your NDR solution.
